In 2021, GitHub launched Copilot as an AI pair programmer embedded in editors (e.g. VS Code), powered initially by OpenAI’s Codex. Over time, Copilot evolved to support multi-model strategies and an “agent” mode—giving it more autonomy in workflows.
With today’s announcement, Copilot is stepping out of the editor into your terminal: GitHub Copilot CLI is now in public preview. That means you can bring the same AI reasoning, editing, GitHub context, and planning capabilities into your shell session.
This shift builds on GitHub’s earlier work with the Model Context Protocol (MCP), used to bridge AI agents with external tools (GitHub itself, file systems, etc.).
In what follows, I walk through features, how to get started, use modes, security trade-offs, and recommended patterns.
Copilot CLI presents a terminal-native AI assistant that understands your codebase and GitHub context.
Key Features
- Terminal-native development: No context switching—you prompt Copilot right in your shell.
- Built-in GitHub integration: You can interact with repositories, issues, pull requests, and branches via natural language.
- Agentic behavior: Copilot CLI can plan multi-step tasks (e.g. refactor, debug, create PRs) under your direction.
- MCP extensibility: It comes with GitHub’s MCP server by default, and you can add custom MCP servers to extend tool access.
- Explicit approval: Whenever Copilot wants to run commands or modify files, it will request your consent first.
You can think of the architecture as:
sequenceDiagram autonumber participant User participant CopilotCLI as Copilot CLI participant Files as Local FS / Tools participant MCP as GitHub MCP Server participant GitHub as GitHub APIs User->>CopilotCLI: Enter prompt CopilotCLI-->>User: Show plan and request approvals CopilotCLI->>Files: Read/modify/execute (on approval) CopilotCLI->>MCP: Invoke GitHub-specific actions MCP->>GitHub: Repos / Issues / PRs requests GitHub-->>MCP: Responses MCP-->>CopilotCLI: Results CopilotCLI-->>User: Diffs, commands, and status
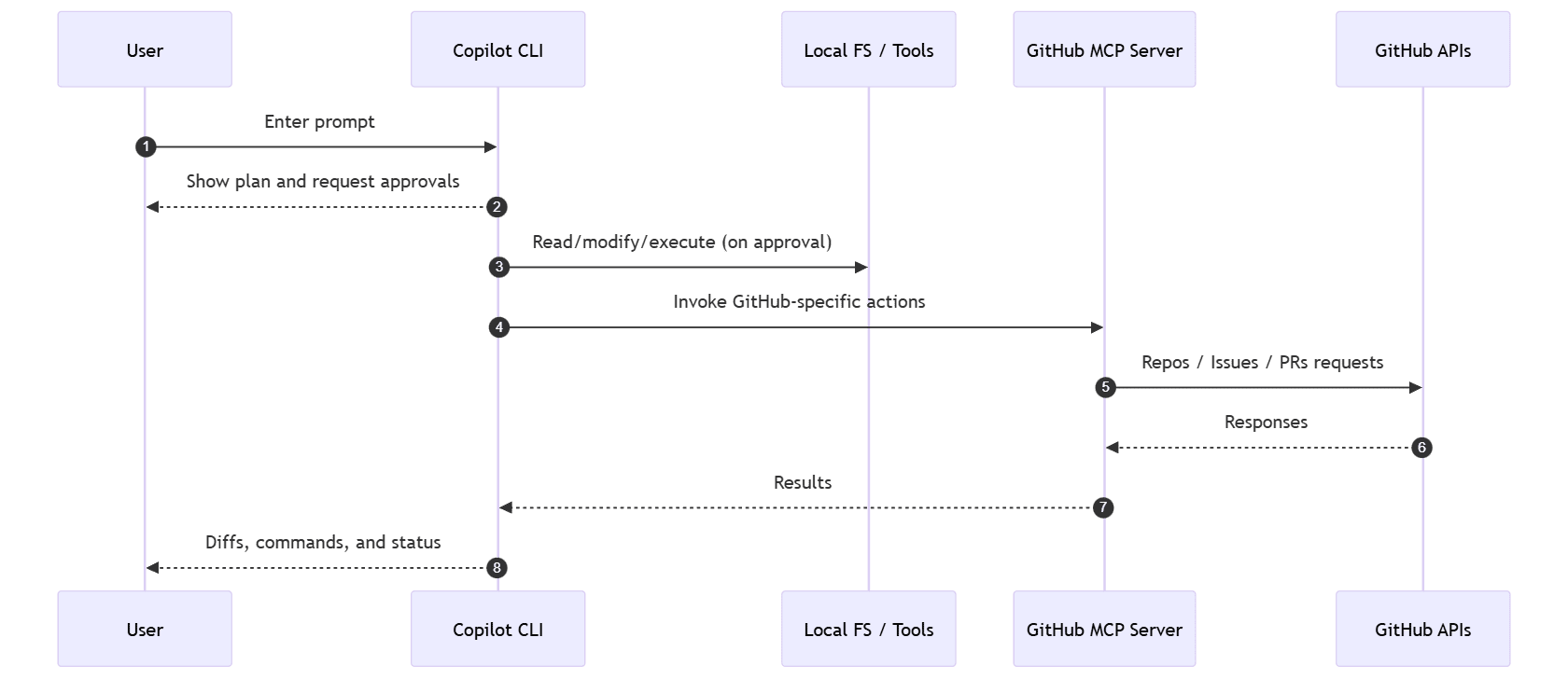
In practice, you’ll stay in your working folder, and Copilot CLI will “understand” the code state, Git commit history, and GitHub context in that folder.
Supported Platforms
- Linux
- macOS
- Windows (via WSL; native PowerShell support is experimental)
Requirements
- Node.js ≥ v22
- npm ≥ v10
- An active GitHub Copilot subscription (Pro, Pro+, Business, or Enterprise)
- If your organization provides Copilot, your GitHub admin must permit CLI usage in policies
Installation & Authentication
To install globally:
npm install -g @github/copilotThen launch:
copilotOn first launch, it prompts you to authenticate with GitHub (via OAuth or PAT). It will also ask whether you trust the current directory (so it can read, modify, or execute files).
If you approve, Copilot can later request tool use (e.g. chmod, sed, node) — but you retain control over every action.
Modes & Usage Patterns
Copilot CLI supports at least two operating modes.
- Interactive mode (default): You enter
copilotand engage in a session where you can prompt, refine, and iterate. - Programmatic mode: You pass a single prompt with
-por--prompt, e.g.:copilot -p "List open PRs in this repo" --allow-all-toolsUse--allow-all-tools(or other approval flags) if you permit Copilot to execute or touch files without repeated prompts.
Within both modes, you can refer to specific files using @path/to/file so Copilot reads their content as context.
Also, you may extend or configure MCP servers (local or remote) to give Copilot access to more capabilities beyond GitHub.
Security & Safety Considerations
Because Copilot CLI is a powerful local agent, security is nontrivial:
- You must explicitly trust each directory where Copilot runs (so it won’t invade arbitrary paths).
- MCP and agent workflows carry attack surface: tools accessible through MCP servers may be abused. Recent audits show risks of code injection, credential exposure, and tool-poisoning attacks in generic MCP setups.
- Always review recommended actions before approval.
- Only add MCP servers from trusted sources; audit what tools those servers expose.
As you use Copilot CLI, maintain principle of least privilege: limit tool grants, isolate workspaces, and monitor logs.
What’s New / Future Directions
Some of the newest capabilities enabled by Copilot CLI / Copilot ecosystem:
- Copilot now supports creating issues that embed relevant code snippets/files directly.
- The Remote GitHub MCP Server is in public preview—avoiding the need to run a server locally.
- GitHub plans further integration of multiple MCP servers and richer agent capabilities.
Given the public preview status, APIs, behavior, and CLI interface may evolve. Use feedback channels and watch updates.
Quickstart Example
Here’s how a basic dev session might flow:
- Navigate into a cloned GitHub repo.
- Run
copilotin terminal. - Approve directory trust.
- Prompt:
What are the open issues related to logging performance in this app? - Copilot responds, optionally fetching issue list, code files, etc.
- Ask for a patch:
Improve logging in src/logger.js to include timestamps, handle edge cases. - Copilot proposes changes; you review, accept or modify.
- Ask:
Create a pull request with these changes.
Behind the scenes, Copilot uses the MCP GitHub server to open the PR.