DNS—short for Domain Name System—was created in the early 1980s to replace brittle host files and make Internet naming scalable and decentralized. Paul Mockapetris designed the core architecture, later standardized in RFCs 1034 and 1035, which define the hierarchical namespace, resource records, and the separation between authoritative servers (holders of truth for a zone) and resolvers (clients that find that truth). This separation, plus caching with time-to-live (TTL), let a global, federated phonebook evolve without a central bottleneck. Today, the same design still underpins every page load—augmented by extensions such as EDNS(0), DNSSEC, and encrypted transports.
When you type a name in your browser, your operating system’s stub resolver forwards the query (e.g., A/AAAA for an IP) to a recursive resolver—often run by your ISP, an enterprise, or a public service. That resolver performs iterative lookups from the DNS root down to the domain’s authoritative servers, caching along the way. Authoritative servers answer for their zones (for example, the nameservers of dropletdrift.com), while the resolver assembles the final answer for your browser. This division of labor—recursive discovery versus authoritative truth—is foundational to DNS’s performance and scalability.
The journey: from your browser to the web server
Below is the resolution flow for www.dropletdrift.com as you experience it on a modern system. Pay attention to the recursion and caching you’ll encounter again when we discuss performance and resilience.
sequenceDiagram
autonumber
participant U as Browser (Stub)
participant R as Recursive Resolver
participant ROOT as Root (.)
participant TLD as .com NS
participant AUTH as dropletdrift.com NS
participant WEB as Web Server (A/AAAA target)
U->>R: Query: www.dropletdrift.com A
alt Cache hit
R-->>U: IP from cache (valid TTL)
else Cache miss
R->>ROOT: NS for .
ROOT-->>R: Referral to .com (NS + glue)
R->>TLD: NS for dropletdrift.com
TLD-->>R: Referral to dropletdrift.com (NS + glue)
R->>AUTH: A for www.dropletdrift.com
AUTH-->>R: Answer: A 93.184.216.34 (TTL)
R-->>U: Final answer (and caches)
end
U->>WEB: TCP/TLS to 93.184.216.34:443
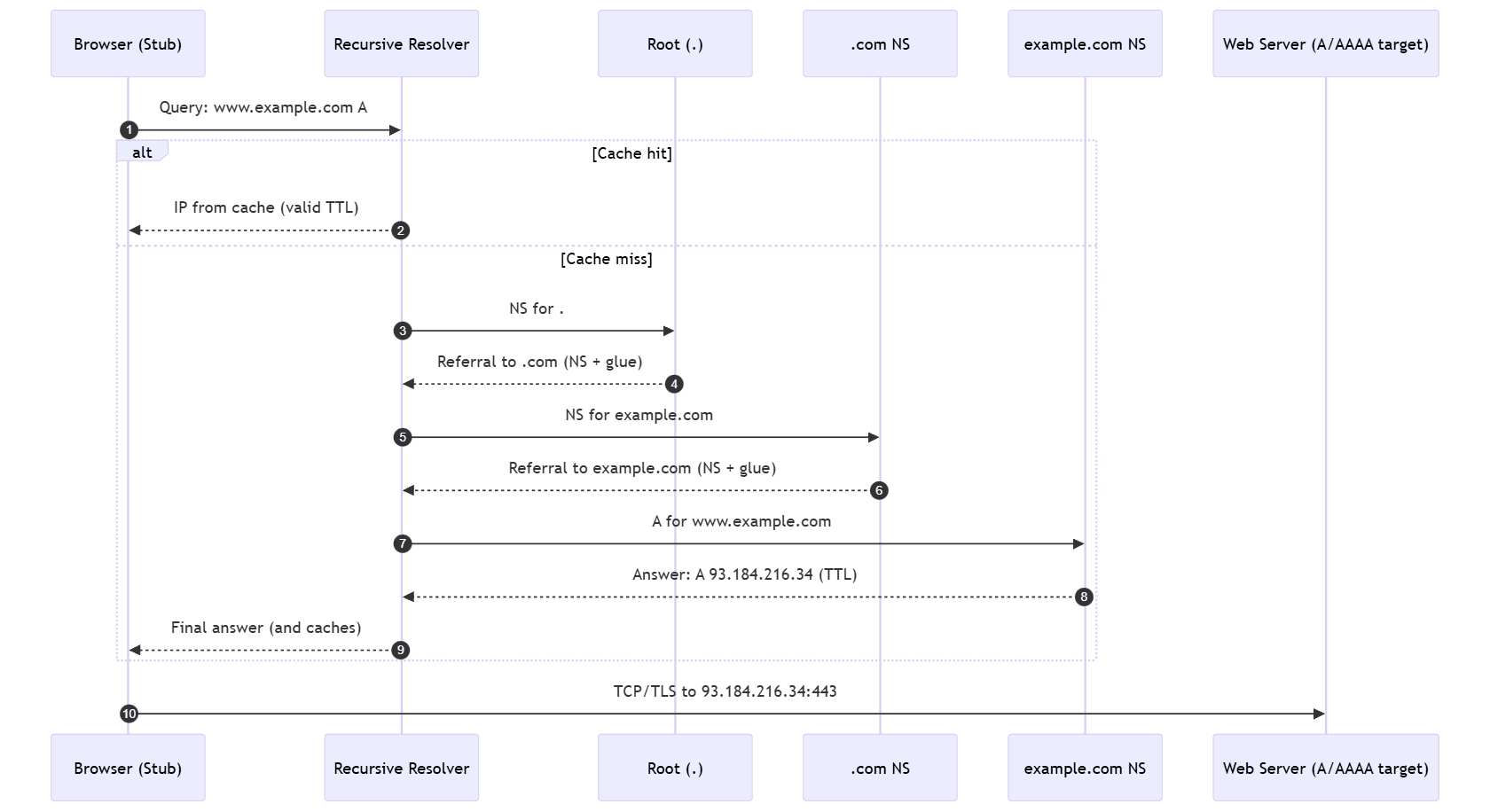
Why this works fast: the resolver caches answers according to each record’s TTL, so subsequent users may get instant responses without repeating the full walk. RFC 8767 even allows serving “stale” cached data briefly during upstream outages to improve resilience.
Where the hierarchy starts: the root and its operators
The resolver begins with priming—learning the current list of root server names (a.root-servers.net … m.root-servers.net) and their addresses. Those 13 identities are operated by 12 independent organizations and are anycast to more than 1,500 server instances worldwide, providing low latency and robustness. In March 2025, RFC 9609 updated the best current practice for priming, replacing RFC 8109.
Historical note: limiting DNS messages to 512 bytes over UDP originally constrained how many root servers could be listed in responses; EDNS(0) later raised those limits safely.
What your resolver actually asks: minimization and EDNS
Classic resolvers sent the full domain name to each tier, but modern privacy-aware resolvers use QNAME minimization: ask the root only about .com, then ask the .com servers only about dropletdrift.com, and so on, reducing leakage of the complete name to unnecessary parties. EDNS(0) (Extension Mechanisms for DNS) extends DNS without breaking compatibility—most notably by allowing larger UDP messages to carry DNSSEC data and additional options.
Authenticity, not secrecy: what DNSSEC adds
By default, DNS is unauthenticated plaintext. DNSSEC signs zones so resolvers can validate that responses are authentic and unmodified, using a chain of trust from the signed root to the queried zone. DNSSEC does not encrypt traffic; it provides origin authentication and integrity. Validating resolvers set the AD (Authenticated Data) bit when answers check out, and they treat tampered data as bogus.
Example: validating DNSSEC with dig
dig +dnssec www.nic.cz A
# Look for the "ad" flag in the header and RRSIG records in the answer/authority sections.Confidentiality in transit: DoT and DoH
To hide queries from on-path observers and prevent trivial manipulation between your device and the resolver, you can encrypt the transport:
- DNS over TLS (DoT) wraps DNS in TLS on port 853, giving confidentiality and integrity for queries to your chosen resolver.
- DNS over HTTPS (DoH) sends DNS messages over HTTPS, often on port 443, using standard HTTP semantics (GET/POST). Major public resolvers support RFC 8484.
Example: querying a DoH endpoint with curl
# Base64url-encoded DNS message for "dropletdrift.com A" (illustrative):
curl -s -H 'accept: application/dns-message' \
'https://dns.google/dns-query?dns=AAABAAABAAAAAAAAB2V4YW1wbGUDY29tAAABAAE'As noted earlier, DoT/DoH protect the path to the resolver; DNSSEC protects the content back to the zone’s keys. Using both gives confidentiality in transit and authenticity at the source.
Caching, TTLs, and “negative” answers
Every positive response carries a TTL that bounds how long it may be cached. Negative responses (e.g., NXDOMAIN or “no data”) are cacheable too; their lifetime comes from the zone’s SOA MINIMUM field (per RFC 2308’s updated definition). Modern resolvers may also serve stale data briefly during upstream issues, trading a short window of potential staleness for uptime. When we looked at the resolver’s journey earlier, this caching is why repeats are fast and why changes may take time to propagate.
Example: observing TTL behavior with dig
dig www.dropletdrift.com A +ttlunits
# Run the same command a few seconds later to see TTL decrement until expiry.What happens on failures
- Timeouts or lame delegations: the resolver retries over UDP (and sometimes TCP) against alternate servers in the NS set.
- DNSSEC validation failure: the resolver returns SERVFAIL to the client rather than an unauthenticated answer.
- Outages upstream: with RFC 8767 enabled, resolvers may serve stale cache entries temporarily to keep applications running. As before, the implication is that robust resolvers smooth over transient problems without hiding genuine integrity failures.
From theory to your machine
On most systems, your stub resolver learns its recursive resolver via DHCP or manual configuration. Some platforms run a local caching stub (e.g., systemd-resolved or unbound) and then forward to an upstream recursive. You can always see where queries go with a trace:
dig +trace www.dropletdrift.com
# Follows the chain: root -> TLD -> authoritative -> final answerPutting it together: performance, privacy, and trust
Practically, you get speed from caching and anycasted infrastructure at the root and TLDs; you get integrity from DNSSEC; and you get confidentiality in transit from DoT or DoH. Minimization reduces unnecessary data sharing with intermediaries. Choosing a recursive resolver that validates DNSSEC, implements QNAME minimization, and supports encrypted transports moves you closest to those ideals without changing the web server you visit. At this point, you can revisit the sequence diagram above and map each property—cache, validation, encryption—to a step you now understand.
References (selected)
- Mockapetris P. RFC 1034/1035: Domain Names (concepts, facilities, implementation). [IETF Datatracker]
- ICANN/IANA. Root Server System overview; list of root servers (operators, anycast footprint). [ICANN]
- Koch et al. RFC 9609: Initializing a DNS Resolver with Priming Queries (obsoletes RFC 8109). [RFC Editor]
- Damas, Graff, Vixie. RFC 6891: EDNS(0) (larger messages, extension mechanism). [IETF Datatracker]
- Arends et al. RFC 4033/4034/4035: DNSSEC (authenticity and integrity). [RFC Editor]
- Hu, Zhu, Heidemann. RFC 7858: DNS over TLS; Hoffman, McManus. RFC 8484: DNS over HTTPS. [IETF Datatracker]
- Bortzmeyer et al. RFC 9156: QNAME Minimisation (privacy in queries). [IETF Datatracker]
- Andrews. RFC 2308: Negative Caching of DNS Queries; IETF. RFC 8767: Serving Stale Data. [IETF Datatracker]
Quick glossary
Stub resolver: the OS library that sends your app’s DNS question to a recursive resolver.
Recursive resolver: a server that chases down the answer across the hierarchy and caches it.
Authoritative server: the server that owns the data for a zone and returns the canonical answer.
TTL: the time a cached answer remains valid before re-querying.
DNSSEC: cryptographic signatures on DNS data for origin authentication and integrity.
DoT/DoH: encrypted transports between client and resolver.










