DNS’s original goal was to convert human-friendly names (like dropletdrift.com) into machine addresses (IP). In parallel evolved a “reverse” function—mapping an IP back to a name. Though not strictly required, reverse DNS (rDNS) has been recommended as a sound best practice since early DNS guidance (e.g. Informational RFCs). Over time, especially with email and network operations, rDNS took on more real-world weight. Just as forward DNS needs A, AAAA, or CNAME records, reverse DNS primarily uses PTR (pointer) records in special DNS zones.
In what follows, I’ll walk you through how reverse DNS actually works (for IPv4 and IPv6), how it’s delegated, how lookups proceed, and where it matters—especially in email, diagnostics, and reputation. Along the way, you’ll see overlaps with forward-confirmed rDNS (which we touched on earlier in aliasing and record matching).
How reverse DNS is structured: PTR, ARPA zones, and delegation
PTR record and naming convention
A PTR record maps an IP address (in reversed form) to a canonical hostname. It is the counterpart to A/AAAA: instead of name → IP, PTR gives IP → name.
For IPv4, the naming convention is:
- Reverse the octets of the address (e.g.
192.0.2.25→25.2.0.192) - Append the suffix
.in-addr.arpa - Store the PTR record at that name, pointing to the hostname
Thus:
25.2.0.192.in-addr.arpa. IN PTR host.dropletdrift.com.IPv6 does the same in nibble form (hex digits), reversed, under .ip6.arpa.
Delegation and control
Because IP address blocks are allocated hierarchically (e.g. to ISPs, organizations), control of PTR zones flows similarly. For IPv4, the address owner (or their upstream provider) must hold the reverse zone (or a delegated slice thereof) to publish the PTR. Many times you must ask your ISP or cloud provider to set or delegate the reverse DNS.
In IPv4, classless reverse delegation (RFC 2317) allows delegation of sub-/24 blocks via CNAMEs.
The lookup process: from IP to name
Here’s the stepwise flow of a reverse lookup:
sequenceDiagram participant Client participant Rec as Recursive Resolver participant Root participant ARPA participant Zone as PTR Zone (ISP or org) participant Host Client->>Rec: PTR query for reversed IP + .in-addr.arpa / .ip6.arpa Rec->>Root: referral for corresponding in-addr.arpa or ip6.arpa Root-->>Rec: NS for in-addr.arpa / ip6.arpa Rec->>ARPA: query reversed IP in that domain ARPA-->>Rec: NS delegation to PTR zone owner Rec->>Zone: request PTR record Zone-->>Rec: PTR → canonical host name Rec-->>Client: final name
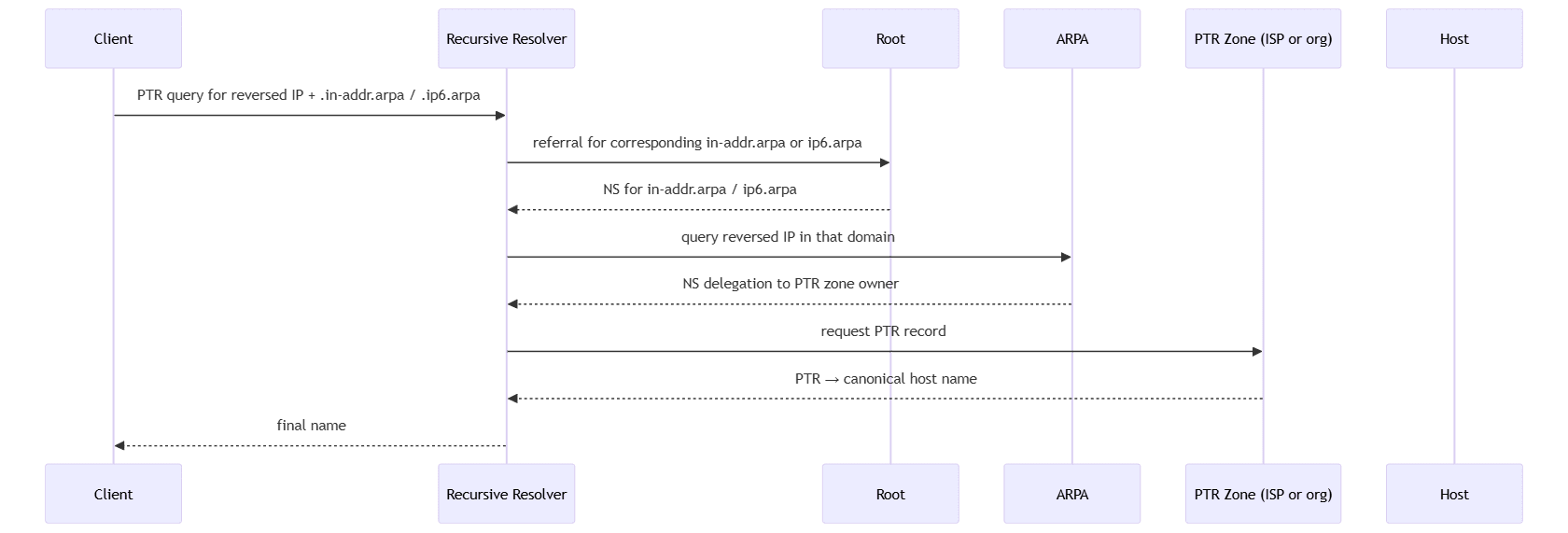
Under the hood, the resolver must traverse from root into the in-addr.arpa (or ip6.arpa) tree, following delegations until it reaches the authoritative PTR zone, then retrieve the PTR record.
If there is no PTR record for that IP, the lookup yields “no record” (NXDOMAIN or NODATA).
Forward-confirmed rDNS (FCrDNS) and why matching matters
A reverse lookup alone tells you “this IP maps to this hostname.” But trust increases if a forward lookup confirms that hostname maps back to the same IP. That pattern is called forward-confirmed reverse DNS (FCrDNS).
When both sides match, many systems treat it as a weak but useful validation of consistency between the name owner and the IP owner. Email systems often use FCrDNS as part of anti-spam heuristics.
However, FCrDNS is not a formal standard requirement and cannot alone prove ownership—it’s one of several signals.
Why reverse DNS matters: use cases and implications
Email deliverability and spam filtering
Many mail servers will reject or flag incoming mail from IPs without valid PTRs or that fail FCrDNS. The rationale: a well-configured mail server ought to present a reverse name matching its forward name, which suggests legitimacy.
A missing or mismatched PTR can contribute to messages being dropped or diverted to spam.
Diagnostics, logging, and visibility
Network tools (e.g. traceroute, ping, syslog) often produce logs of IP addresses. Reverse DNS lets those logs show names instead, improving readability and context in diagnostic workflows.
System administrators often configure PTRs for internal IPs to ease debugging and tracing.
Reputation and trust
In ecosystems like email and even some network services, a consistent reverse/forward mapping contributes to the reputation of servers. PTR usage signals care in configuration, and is often treated as a positive metric in deliverability scoring.
In contrast, misconfigured or stale PTRs can leak information about network structure or expose device dynamics (a privacy risk described in recent research).
Pitfalls, limitations, and best practices
- Control limitations: You often don’t control reverse zones unless assigned that block. Achieving PTR setup may require coordination with your ISP or provider.
- Partial or missing entries: Some IPs lack PTRs or have generic placeholders (e.g.
123-45-67-89.dynamic.isp.net). That’s valid but weaker in trust. - Multiple PTRs: DNS allows more than one PTR per IP, but it’s rare, and large responses risk fragmentation.
- Asymmetry problems: If reverse and forward don’t match, many email systems downgrade trust or reject the connection.
- Privacy exposure: Some networks automatically expose client identities via reverse DNS changes; this may reveal patterns of usage over time.
- IPv6 complexity: The nibble reversal and large address space make PTR setup more tedious, but essential when using IPv6 addresses.
Best practices summary:
- Always request or configure a PTR record for any public IP you use for outbound email or services.
- Ensure your forward (A/AAAA) record for the hostname returned by the PTR points back to the same IP (i.e. achieve FCrDNS).
- Use static or stable IPs for services requiring reverse DNS; avoid PTRs for highly dynamic addresses.
- Monitor and periodically verify PTR correctness, as misconfigurations can break quietly under updates.










